Additional Security Training
Deepen your team’s cybersecurity expertise with advanced certifications that prepare them to lead, audit, and secure modern digital ecosystems.

Companies grow with a more skilled team thanks to our training programs




Course Overview
The Additional Security Training Program strengthens your organization’s defense posture by equipping professionals with advanced certifications in information security management, auditing, cloud security, and risk control.
These globally recognized courses are designed for cybersecurity leaders, auditors, and analysts looking to gain the expertise and credentials needed to safeguard critical information systems and infrastructure.
Who This Course Is For
- Information security and risk management professionals
- IT auditors and compliance officers
- System administrators and cybersecurity managers
- Organizations seeking to upskill teams in advanced security frameworks
Learning Outcomes
After completing this training, participants will be able to:
- Design and manage enterprise-level security frameworks
- Audit and assess information systems for compliance and resilience
- Implement effective risk management and mitigation strategies
- Prepare for globally recognized security certifications such as CISM, CISA, CISSP, and CRISC
What’s Included
Below are the specialized courses included under the Additional Security Training catalog
Developed using the methodology that prepares cadets for the Israeli Cyber and Intelligence Unit, this course helps learners understand and mitigate human error while building advanced defensive skills against common cyber threats.
Prepare for the ISACA CISM certification and validate your ability to manage and support the security needs of an enterprise with globally recognized credentials.
Gain the expertise to audit, control, and secure enterprise information systems. This course prepares you for the ISACA CISA certification exam and strengthens your organization’s data integrity.
Learn the eight domains of the CISSP Common Body of Knowledge (CBK) and acquire the advanced technical and managerial skills needed to design and manage secure enterprise environments.
This edition deepens your understanding of the CISSP framework with a job-focused approach to security processes and certification readiness.
Master the principles of risk management, from identification to mitigation and control implementation, with ISACA’s CRISC certification.
Apply globally recognized PMI practices to identify, assess, and control project risks. This course prepares you to earn the PMI-RMP certification and manage uncertainty across projects.
Get comprehensive coverage of cloud security principles and best practices. This prep course explores all six domains of the (ISC)² CCSP Common Body of Knowledge (CBK) to help you design and manage secure cloud environments.
Why Choose Us
Industry-Recognized Certifications
Train for credentials from ISACA, PMI, and (ISC)² — trusted by cybersecurity professionals worldwide.
Expert-Led Instruction
Learn from certified trainers with years of practical security and risk management experience.
Comprehensive, Real-World Curriculum
Courses combine theory, simulation, and certification prep for immediate job relevance.
Flexible Learning
Choose in-person, online, or hybrid learning to suit your team’s schedule and goals.

Our Unique Advantage
At NexTechBreedge, we turn cybersecurity from a concern into a culture. Our training empowers your people to think critically, respond swiftly, and protect your systems confidently


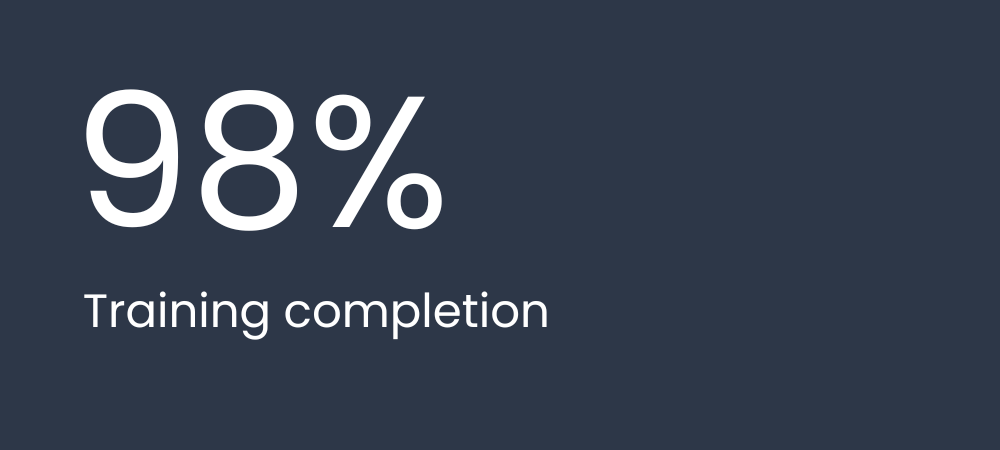

50%
Fewer admin hours

Testimonial

Empower your workforce with our Training Programs
Speak to our Training Experts to customize a security learning path that aligns with your organization’s goals.




Additional Security Training
Take a look below at the various courses we offer
under the Additional Security training catalog
Cybersecurity Essentials
Cybersecurity Essentials was developed using unparalleled learning methodology that prepares cadets for the Israeli Cyber and Intelligence Unit. It is designed to tackle human error by helping develop an advanced understanding and skills to protect individuals and organizations against the most common cyber threats.
Certified Information Security Manager (CISM)
This course is designed to help candidates prepare for sitting the ISACA CISM certification examination. By taking this course and obtaining CISM certification, your experience and skills in supporting the information security needs of your organization will be validated.
Certified Information Systems Auditor (CISA)
This course is designed to help candidates prepare for sitting the ISACA CISA certification examination. By taking this course and obtaining CISA certification, your experience and skills in auditing and securing the organization’s information systems will be validated.
Certified Information Systems Security Professional (CISSP)
In this course, students will expand upon their knowledge by addressing the essential elements of the 8 domains that comprise a Common Body of Knowledge (CBK) for information systems security professionals.
Certified Information Systems Security Professional (CISSP) Sixth Edition (v1.1)
This course addresses the essential elements of the eight domains that comprise a Common Body of Knowledge (CBK) for information systems security professionals. The course offers a jobrelated approach to the security process, while providing a framework to prepare for CISSP certification.
CRISC Certified in Risk and Information Systems Control
The CRISC course is designed for those who have experience with risk identification, assessment, and evaluation; risk response; risk monitoring; information systems control design and implementation; and information systems control monitoring and maintenance.
Risk Management Professional (PMI-RMP) Certification
In this course, students will apply the generally recognized practices of project risk management acknowledged by the Project Management Institute (PMI) to manage project risks successfully.
CCSP Certification Prep Course
This course is the most comprehensive review of cloud security concepts and industry best practices covering the six domains of the CCSP Common Body of Knowledge (CBK).

