Apple Productivity Training
Empower your team with the skills to deploy, manage, and support Apple devices for seamless productivity across iOS and macOS environments.

Companies grow with a more skilled team thanks to our training programs




Course Overview
The Apple Productivity Training Program equips IT professionals, business users, and administrators with the practical skills to integrate, manage, and support Apple devices in modern workplace environments. Participants will learn how to configure iOS and macOS systems, deploy devices efficiently, and ensure smooth cross-platform compatibility.
Who This Course Is For
- IT administrators and technical support professionals
- Businesses deploying or managing Apple devices
- Teams operating hybrid (Apple + Windows) environments
- Professionals responsible for device setup, security, or troubleshooting
Learning Outcomes
After completing this training, participants will be able to:
- Configure, manage, and supervise iOS devices at scale
- Integrate macOS systems within Windows-based networks
- Deploy Apple devices efficiently using best practices and management tools
- Troubleshoot and support macOS systems using built-in recovery and command-line tools
- Optimize Apple technology to enhance workplace productivity and security
What’s Included
Below are the specialized courses included under the Apple Productivity Training catalog
Gain the knowledge and tools needed to deploy and manage iOS devices effectively. Through hands-on exercises, learn how to configure, supervise, and secure iOS systems for business use.
Explore the full potential of iPads in the workplace. Learn to navigate iOS, customize settings, manage apps, and integrate the device seamlessly into daily workflows.
Train your team on how to successfully integrate Mac computers into existing Windows or standards-based networks. Understand macOS compatibility, file sharing, and account management in mixed environments.
Develop the skills to install, configure, and troubleshoot macOS systems. This course also covers advanced tools such as macOS Recovery and the command-line interface for effective system management.
Why Choose Us
Hands-On Labs
Practice real deployment, integration, and troubleshooting tasks in simulated Apple environments.
Certified Apple Instructors
Learn directly from Apple-certified professionals with extensive enterprise experience.
Cross-Platform Focus
Master integration across Apple, Windows, and other business systems.
Flexible Learning
Choose onsite, virtual, or blended training to match your team’s needs.

Our Unique Advantage
At NexTechBreedge, we help businesses use everyday tools to improve efficiency. Our Business Productivity Training doesn’t just teach shortcuts. It helps your people discover smarter ways to work, collaborate, and deliver results that move the business forward.


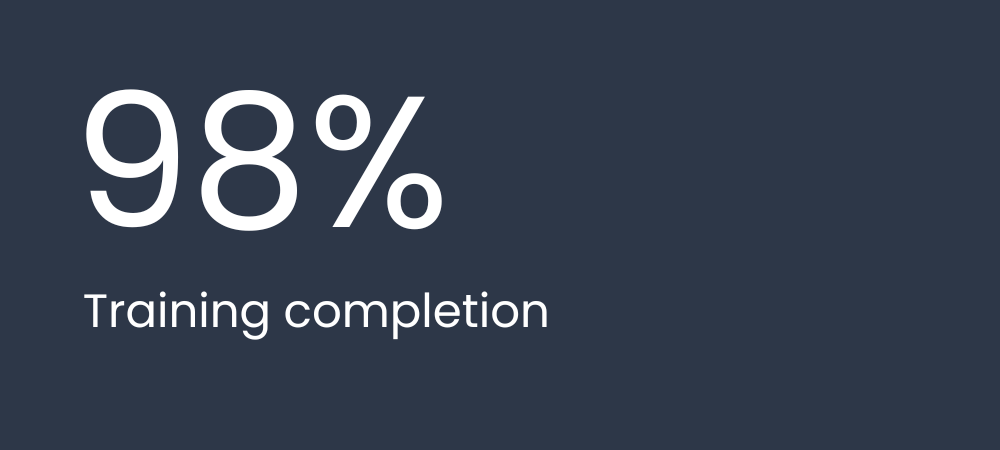

50%
Fewer admin hours

Testimonial

Empower your workforce with our Training Programs
Connect with our Training Experts to design a tailored Apple learning path that fits your organization’s needs.




Apple Productivity Training
Take a look below at the various courses we offer
under the Apple Productivity training catalog
iOS Deployment Essentials
This two-day course provides students an opportunity to learn about the skills, tools, and knowledge needed to deploy iOS devices. Interactive discussions and hands-on exercises guide students through the configuration, management, and supervision of iOS.
iPad For Business
This day-long workshop gives participants a thorough understanding of the iPad iOS operating system. This course is designed for both those who want to learn more about their iPads.
Mac Integration Basics
Companies are increasingly integrating Mac computers into Windows or other standards-based network environments. This two day Mac Integration Basics course examines how to best use a Mac(s) in an organization that predominantly functions with a Microsoft Windows.
MacOS Support Essentials
Participants in this course will learn how to update, upgrade, and reinstall the macOS then set up and configure the new macOS. They will also be introduced to the command-line interface and macOS Recovery.

